How to be anonymous on the Internet
This document has been created for users who are concerned about others monitoring their Internet browsing or want to remain anonymous while they browse the web. Keep in mind that there are different degrees of anonymity and even following these steps do not guarantee 100% anonymity. If you're attempting to conceal your identity to do something illegal or inappropriate while on the Internet, this document is not for you.
Below is a list of different methods to help protect your identity while on the Internet.
Privacy basics
For most users following some basic rules can help with your anonymity on the Internet.
- Do not disclose any private information, unless absolutely required. In some cases when it is required such as your last name, only fill in partial information such as your last initial.
- Don't fall into e-mail and web phishing traps. Become familiar with the signs of phishing and don't disclose private information in e-mail.
- If you're using Microsoft Windows, familiarize yourself with spyware and have at least one program installed to protect the computer.
- Protecting children from harmful material and people on the Internet.
Public Anonymous proxy
When browsing the Internet you're browsing from your computer or router assigned IP address, this IP address can be used to track your general location and can help identify your visit. To help keep your computer anonymous you can use a web based proxy to browse the web. A web based proxy allows you to use an alternate computer to load a website and then display the results on your computer through the browser. Below is a short list of some of the available anonymous web based proxies.
If you're in an area where you feel your connection may be compromised or sniffed (e.g., connecting to the Internet at a WI-FI hotspot). Using a HTTPS proxy is a great way to help encrypt data coming from the proxy to your computer that is not encrypted, helping to prevent any eavesdropping. If you're using a proxy web service such as Proxify, you can also use an HTTPS connection.
If you're using Mozilla Firefox as your browser and find yourself frequently needed a proxy, there are dozens of good proxy add-ons available.
The proxy you're using to browse the Internet may keep a log of visitors. If a legal authority wants to obtain identifying information to locate you, it may be possible. If you are entering sensitive data such as usernames, passwords, credit card information, the person in control of the proxy could capture and use that information.
Boot from Anonym.OS LiveCD
Anonym.OS is a LiveCD that allows a user to boot from a CD and use a variant of OpenBSD that has been designed to help keep a user anonymous while browsing the Internet.
Tor
 Tor was originally developed for the U.S. Navy with the purpose of protecting government communications. Tor works to help protect your privacy by using a network of virtual tunnels to pass information over the Internet.
Tor was originally developed for the U.S. Navy with the purpose of protecting government communications. Tor works to help protect your privacy by using a network of virtual tunnels to pass information over the Internet.Whonix
Whonix is an operating system focused on anonymity, security, and privacy. It consists of two parts: One solely runs Tor and acts as a gateway, the other, is on a completely isolated network.
Alternate computer or connection
Finally, connecting to the Internet using someone else's connection, e.g., cafe, library, school, work, etc. can also keep you anonymous. When using someone else's connection you're logging in as their IP address and not your personal address.
However, keep in mind that if you had to use a login to access the computer or network, that login could be traced back to you.
Private mode or Incognito mode
Most browsers today offer some type of private mode or incognito mode. While this mode will not keep you anonymous to anyone with authority that can request server or search logs it will keep what you do locally anonymous when active.
Other software products
There are also dozens of other non-free software products for users who find the above suggestions don't meet their needs.
Steps to being completely anonymous online

1. Find a safe country that values privacy
It’s good to be in a country that attempts to protect citizens from rampant government spying, at least without legal warrants and judicial oversight. It’s even better to be in a country that at least talks tough about protecting users' individual privacy and places limits on its commercial use.
The European Union’s General Data Protection Regulation (GDPR) is pushing the privacy bar a bit. It impacts any company in the EU or doing business with any citizen in the EU. That’s a lot of coverage. Expect more businesses and countries not in the EU to be moving toward more GDPR-like laws, although you will always have your laggards.
Of course, most of us don’t have the option of simply moving to another, more privacy-embracing country. If that's your situation and if you care about your privacy, be an agent of change. I recommend contributing to any organization that fights for your privacy. Certainly, the Electronic Privacy Information Center (EPIC) and the Electronic Frontier Foundation (EFF) are top organizations with lots of information and a track record of continued hard work and success.
2. Get an anonymizing operating system
Next, you'll need an anonymizing operating system that runs on a resettable virtual machine (VM) running on secure portable media. The portable media device should use hardware-based encryption or a secure software-based encryption program. One of the top products on that list is Ironkey Workspace. It offers good encryption, locks out users who enter too many bad passwords and comes with Microsoft's portable OS, Windows to Go, on several USB key models.
Many privacy advocates prefer a Linux Live distro, such as Tails or ZeusGuard. Live OSes are designed to be booted from removable media for each session, and Tails is one of the best, built for and focused on privacy and security. The U.S. National Security Agency has stated in an internal, leaked presentation that Tails and Live OSes like it are a threat to its eavesdropping mission. That's a ringing endorsement.
Whether or not you use a Live OS, make sure the OS doesn't store information that can be used against you. If you're not using read-only bootable media, consider using a VM solution that resets itself after every use. Better yet, do both. Use a Live OS stored in a VM. Let the VM assign random Dynamic Host Configuration Protocol (DHCP) and (Address Resolution Protocol) ARP addresses on every start.
Also, consider Qubes OS, a free operating system built from the ground up with security as the ultimate objective. It’s used and promoted by some of the world’s biggest privacy advocates. It really is leaps ahead of most operating systems, especially in compartmentalization, meaning that it’s far harder for one compromised program to lead to an entire OS compromise. I fully expect other, more popular OSes, to become more like Qubes in the future, but you can get that functionality now.
3. Use an anonymous VPN
Next, you'll need to connect to the internet using an anonymous method. The best approach would probably be to jump around different open wireless networks, public or otherwise, as much as possible, rarely repeating at the same connection point. Barring that method, you would probably want to use a virtual private network (VPN) or device built for such purposes. There are literally dozens, if not hundreds, of VPNs that are specifically built to make your internet connection more difficult to identify and track. They do this by replacing your computer’s originating IP address and metadata information with something else. Instead they substitute one of their IP addresses for yours and block your metadata information from traveling to the eventual endpoint. On top of that, many privacy-protecting VPNs also promise not to log your connection, so even if they get a legal search warrant from law enforcement, they will have less data that can assist in identifying you.
You can also consider using a device explicitly designed to protect your privacy, like Anonabox and ProxyGambit. Devices like Anonabox can use Tor (covered below) or anonymizing VPN services, which are always on to protect your connection. Devices like ProxyGambit go even a little further. I'll let ProxyGambit describe itself:
ProxyGambit is a simple anonymization device that allows you to access the internet from anywhere in the world without revealing your true location or IP, fracturing your traffic from the internet/IP through either a long-distance radio link or a reverse tunneled GSM bridge that ultimately drops back onto the internet and exits through a wireless network you're nowhere near. While a point to point link is possible, the reverse GSM bridge allows you to proxy from thousands of miles away with nothing other than a computer and internet with no direct link back to your originating machine.
If you are truly concerned about your privacy, then consider using a VPN or anonymizing device to protect your internet surfing.
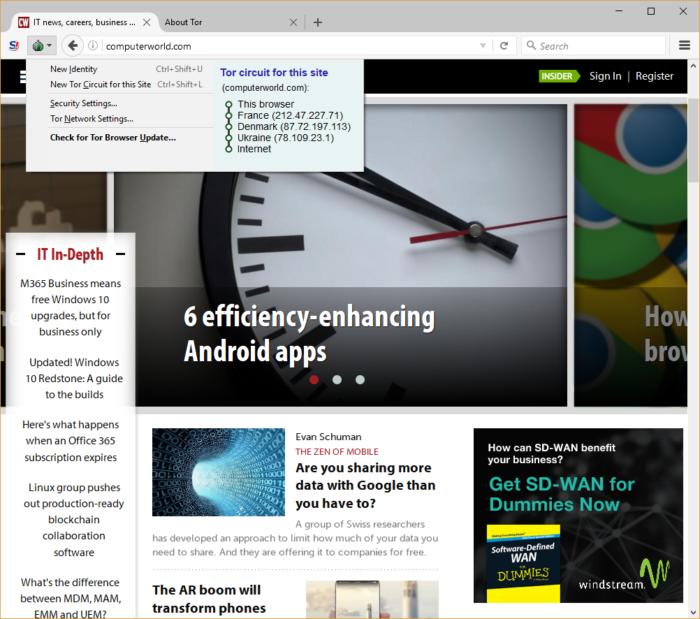
4. Use Tor
Whatever Live OS and internet connection method you use, make sure to go with an anonymizing browser, such as a Tor-enabled browser. Tor is actually an entire system — tools, browsers, APIs and network — dedicated to helping you and your connection remain anonymous.
Once you enter a Tor network path, the traffic to and from your destination will be routed through a random set of "Tor nodes." Although Tor's anonymity can be defeated, it remains one of the best ways to stay anonymous when combined with these other recommendations. You can even buy hardware-based Tor solutions like Anonabox.
5. Don't use plug-ins
It's very important to remember that many of today's browser plug-ins, particularly the most popular ones, leave clues that reveal your identity and location. Don't use them if you want to preserve your anonymity.
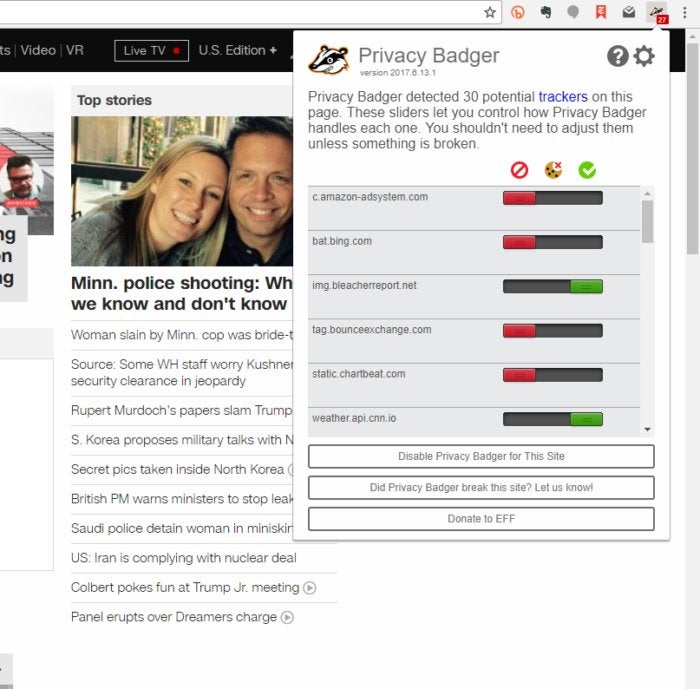
One possible exception would be plug-ins designed to enhance privacy, like Privacy Badger offered by the Electronic Freedom Foundation (EFF). Available for Chrome and Firefox, it stops advertisers and third-party trackers from tracking your web browsing, including what pages you visit. It watches third-party domains that place images, scripts and advertising in web pages you visit, and stops them from tracking you.
Click the Privacy Badger icon in your browser when you’re on a site, and it shows you a list of all the trackers it found. Each tracker is shown as green, red or yellow --- green for those that appear to be safe, red for those that the add-in completely blocked, and yellow for those it partially blocked. The more you browse, the more effective Privacy Badger becomes, because it learns more about the trackers, and so blocks more of them.
Note that Privacy Badger is not a traditional ad blocker, because its intent is to protect your privacy rather than block ads. So, it does block ads that are also used as trackers, but not ads that aren’t related to trackers.
Another EFF plug-in for Chrome, Firefox, and Opera is also worth using. HTTPS Everywhere was written in collaboration with the privacy-focused Tor Project. The plug-in solves a problem with sites that use what should be the secure HTTPS privacy protocol. Some sites that use HTTPS don’t use it properly, so they can default to the unencrypted HTTP protocol. HTTPS Everywhere solves the problem by ensuring they use encrypted HTTPS when you use the plug-in. Note that the plug-in won’t turn normal HTTP connections into encrypted HTTPS connections. It only makes sure that HTTPS connections use encryption properly
6. Stick with HTTPS
When you connect somewhere on the internet, try to use HTTPS. This used to be harder to do, but now the most popular websites use HTTPS by default, and those that don’t can be defeated by using one of the anonymizing VPN services or devices used above. When working with HTTPS, use only handpicked, trusted certificate authorities that don't issue "fake" identity certificates.
7. Avoid the usual applications
Don't install or use normal productivity software, like word processors or spreadsheets. If it’s super popular, they probably don’t care about your privacy. Many "dial home" each time they're started and reveal information. If it’s free and isn’t explicitly designed to protect your privacy, don’t expect any. As computer security guru Bruce Schneier says in his seminal book, Data and Goliath: The Hidden Battles to Collect Your Data and Control Your World, “If something is free, you’re not the customer; you’re the product.”
8. Set up anonymous burner accounts
You'll need a different password and password question answers for each website where you create a logon account. (Note: these steps are not only for privacy nuts and should already be practiced by everyone.) The very paranoid will also want to create different email addresses for each website. These "burner" email accounts are expendable and are much harder to trace back to the real you. Use email services that explicitly advertise as being anonymous. You’ll find free and commercial versions. Always connect to them using other anonymity apps and connections, and switch among burner accounts, even when speaking to the same people.
9. Never use credit cards
If you plan to buy anything on the internet, you can't use a normal credit card and stay anonymous. You can try to use online money transfer services such as PayPal, but most have records that can be stolen or subpoenaed. Better, use an e-currency such as bitcoin or one of its competitors. E-currencies are starting to gain widespread validity and are accepted in more and more places every day. You'll need a bank or service to convert your real money into one of these alternative forms (and to get it back out), but once you're using the currency, buying anonymity is easier to maintain.
10. Test for DNS leaks and browser tracking
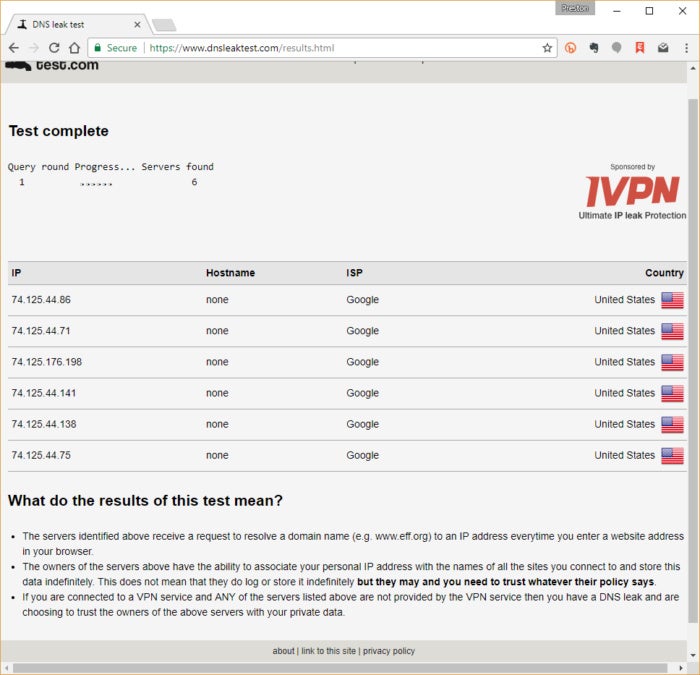
One way to test whether you’re keeping yourself anonymous is to check whether you have a domain name server (DNS) leak. DNS servers translate domain names such as csoonline.com to the numeric IP addresses the Internet uses, such as 151.101.0.230. Internet servicepProviders (ISPs) generally use their own DNS servers, and those servers can be used to identify your and log and track its Internet activities.
VPNs like Tunnel Bear and CyberGhost VPN use DNS servers that protect your anonymity. If you want to make sure you’re protected against DNS leaks, go to www.DNSLeakTest.com. Run the extended test. If you see your ISP’s DNS servers, you’ve got a DNS leak. (The servers should have their name on them --- the leak test identifies them.) If you see the DNS servers run by your VPN provider, you’re safe. If you want help in tracking down and fixing a DNS leak, head to the DNSLeakTest.com page How can I fix a DNS leak? for advice on how to fix it.
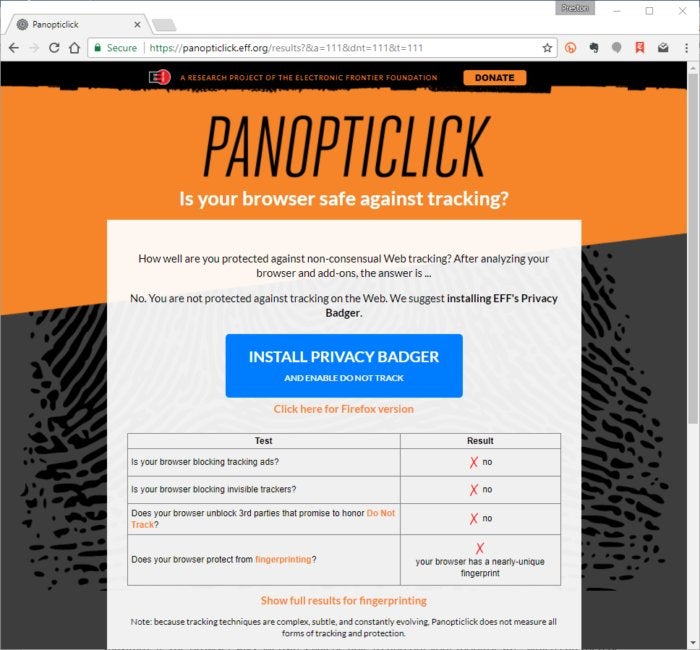
11. Test your overall privacy protection
How well are your privacy actions working? There’s a way to find out by testing how protected you are against being tracked as you browse the web. To do it, head to the EFF’s Panopticlick page and click the big Test Me button. It checks whether your browser is blocking tracking ads and invisible trackers, and whether your browser has a unique fingerprint. Based on the results of what you find on DNSLeakTest.com and Panopticlick, you can rejigger the way you’re trying to protect your anonymity and see how it works, by retesting.

No comments:
Write comments